
FORMAL LeGAL COMPALAINT

👑 El Sayed Mr. 👑
CRIMINAL FRAUD & SURVEILLANCE OPERATIONS
Systematic Law Breaking by Government-Backed Technology Company
⚠️ EVIDENCE SUGGESTS SEJEL TECHNOLOGY OPERATES AS A FRONT FOR SYSTEMATIC FRAUD OPERATIONS ⚠️
Criminal Violations
- •Identity Fraud: Impersonation of bank officials for financial theft
- •Document Falsification: Forged Chamber of Commerce documents
- •Unauthorized Surveillance: Hidden cameras and device access without consent
- •Data Theft: Unauthorized access to personal devices and information
- •Financial Manipulation: Deliberate prevention of bank account access
License & Regulatory Risks
- •Business License Revocation: Criminal operations violate licensing terms
- •Government Contract Termination: Fraud operations compromise public trust
- •Professional Certifications: Engineering council memberships at risk
- •Industry Partnerships: Oracle, AWS, and vendor relationships endangered
- •International Operations: Cross-border fraud may trigger sanctions
AS A GOVERNMENT-BACKED TECHNOLOGY COMPANY, SEJEL TECHNOLOGY'S CRIMINAL OPERATIONS CONSTITUTE A SEVERE BREACH OF PUBLIC TRUST AND MAY RESULT IN COMPLETE LICENSE REVOCATION AND CRIMINAL PROSECUTION OF LEADERSHIP
Incident Period: March 17 - August 31, 2025
COMPANY OWNERSHIP & LEADERSHIP
Ringleader Structure with HR:
Government Backing:
| Category | Details |
|---|---|
| Government Contracts | Saudi government technology contracts |
| Public Sector | Public sector cloud migration projects |
| Professional Bodies | Engineering council affiliations |
| Industry Partners | Oracle and AWS partnerships |
PRIMARY SUSPECT: SEJEL TECHNOLOGY
Critical Timeline Correlation:
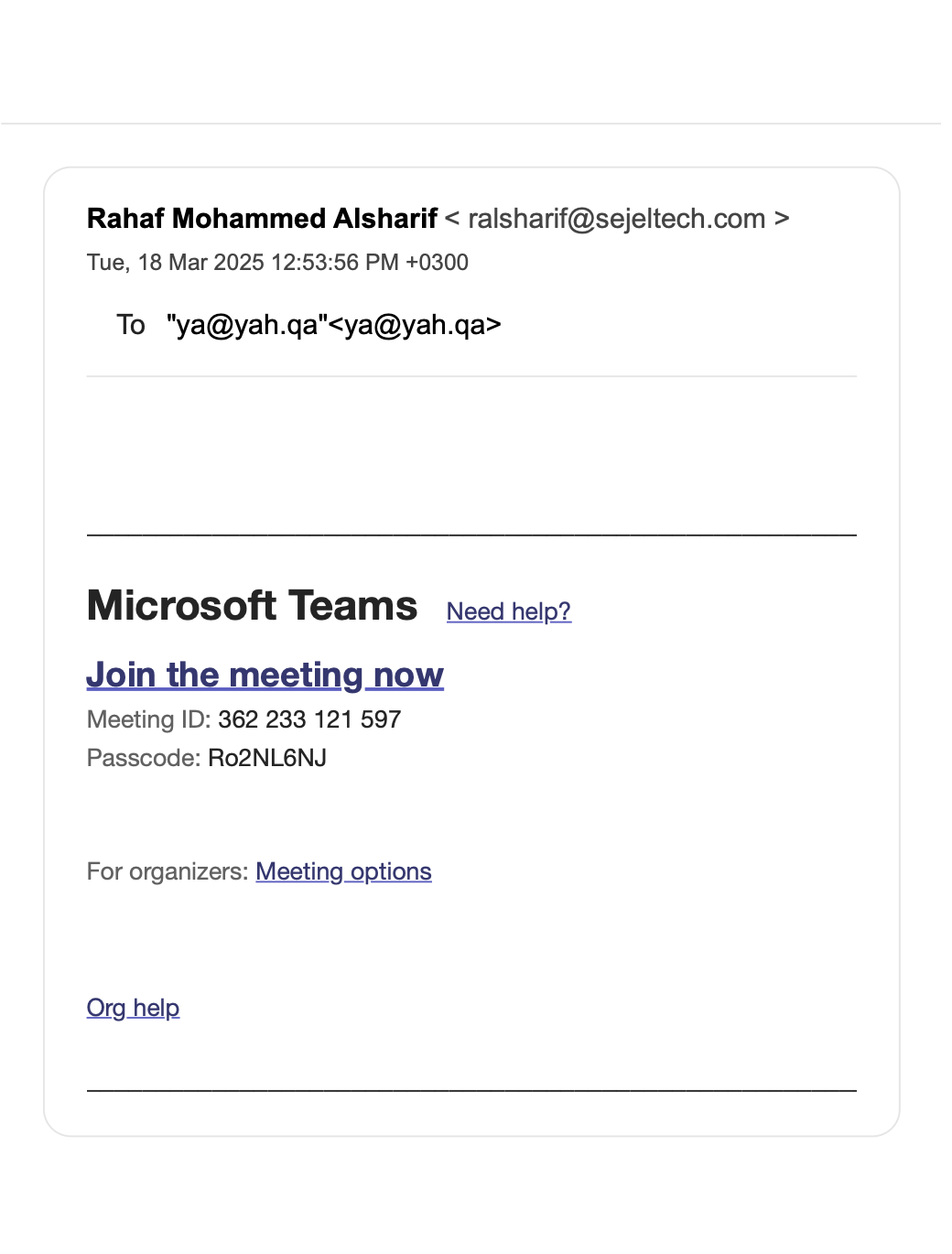
The sophisticated Doha Bank fraud attempt occurred minutes after HR follow-up call the day after the first round interview with Sejel Technology. The caller knew intimate details only shared with Sejel during the interview process, including QID cancellation status.
HR Call Minutes Evidence:
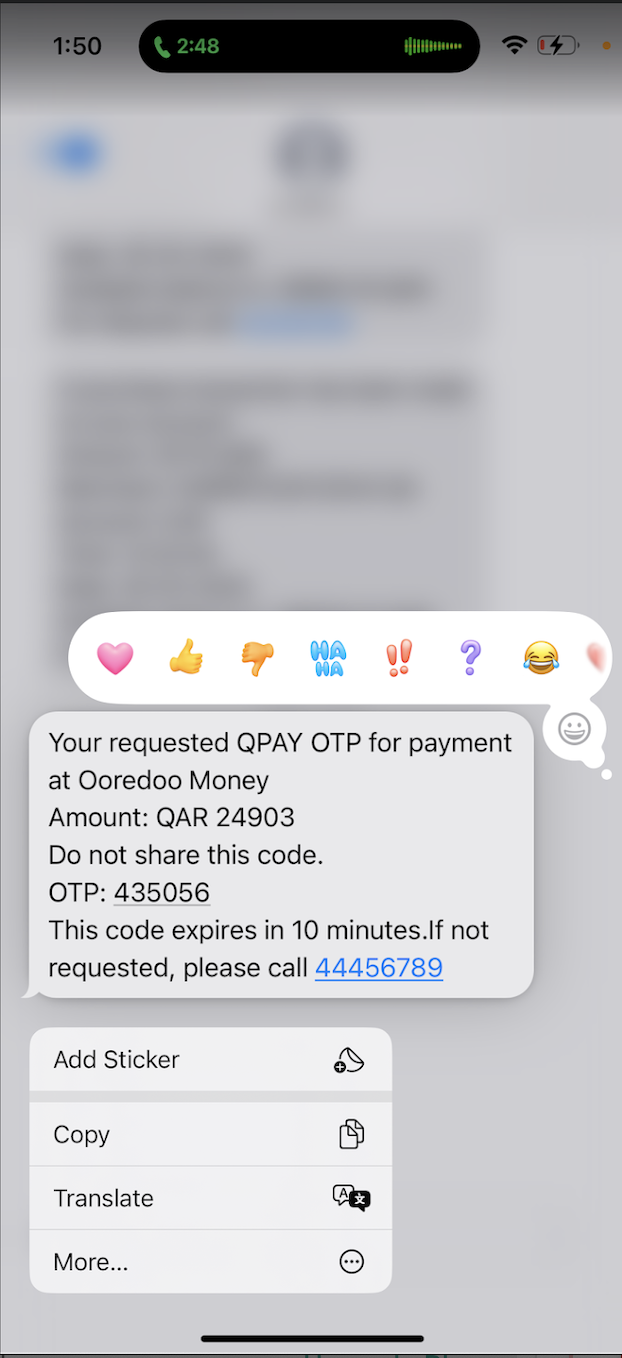
OTP Fraud Evidence Screenshot
Original available for delivery from phone system
Falsified Letter Evidence:
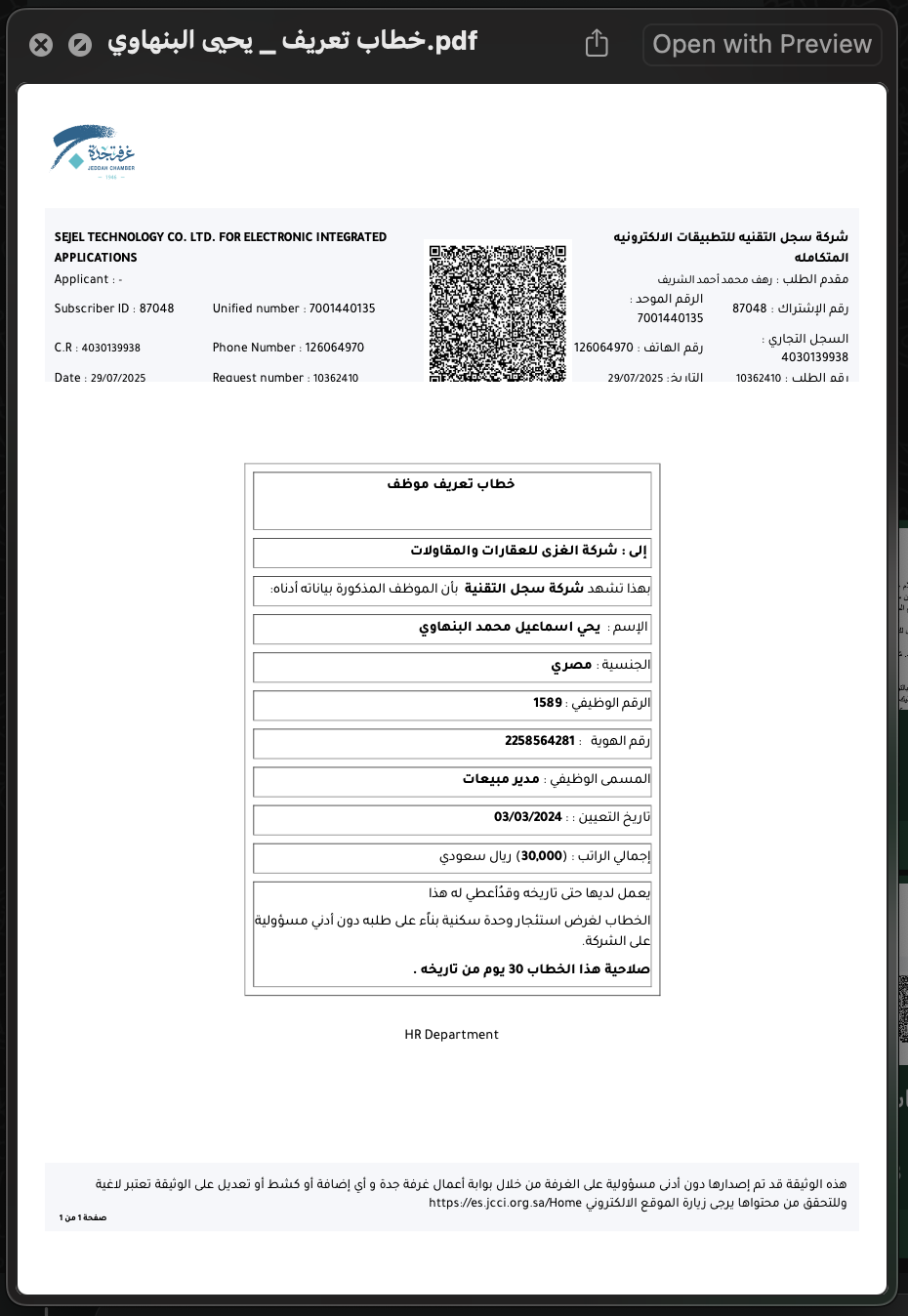
Yahya Banhawi Letter Scheme
Sejel orchestrated a calculated scheme using Yahya Banhawi's letter as a manufactured pretext for termination. They falsified dates from the Chamber of Commerce to make it appear authentic, strategically placed him behind the victim after his June 25th arrival (post-employment start), and used his letter pinned to the victim's name to elaborate on termination proceedings.
Package Delivery Deception
On the day of receiving AWS Community Builder package, an additional shipment addressed to "Mohammed" was delivered with claims it contained gold. This appeared to be an attempt to trick the victim into accepting suspicious packages alongside legitimate deliveries.
Package Delivery Evidence:

OPERATIONAL PERSONNEL INVOLVED IN CRIMINAL ACTIVITIES

Role: Senior leadership coordination

Role: Executive oversight of operations

Role: Delivery operations management

Phone: +966 59 888 2821
Role: Called before the crime call to weaken defense

Phone: +966 50 012 3476
Role: Coordinated in the OTP crime

Phone: +966 54 145 5014
Role: A rejection resource for his name (Alaa = "No" in Arabic). Name changed to AbdulHai. Victim might be target of snipping attack remotely to shut down the case.

Phone: +966 50 647 7416
Role: Coordinated the phones data theft in kharaj gov

Phone: +966 56 195 7590
Role: Conducted the MacBook lunch theft and MacOs takeover by seprating the victim from his machine.
Phone: +966 53 699 5517
Role: Coordinated lunch with Yahya Banhawi for the MacOS takeover.

Phone: +966 54 615 1515
Role: Involved in capturing the victim during employment sneakily and sent to Jeddah. Now at Group-IB Singapore and Turkey.

Phone: +966 59 638 1234
Role: Hired a week before the victim to elaborate on once in Saudi Arabia for the victim. Based in Eastern Province in purpose.

Phone: +966 56 604 0079
Role: Added after the victim managed to run from the airport. He was placed after the victim reached the kingdom.

Phone: +966 53 895 2406
Role: Joined pre-victim landing on the kingdom once he ran due to his softness (the way the victim was led out of the fraud attempt—through a combination of softness and logic). He is identified as number 25, based on the initial offer given to the victim of 25K SAR, and is referenced as "Mohamed Mohamed" (as in Mo Hamed Mo Hamed, meaning "not thankful" in Arabic).
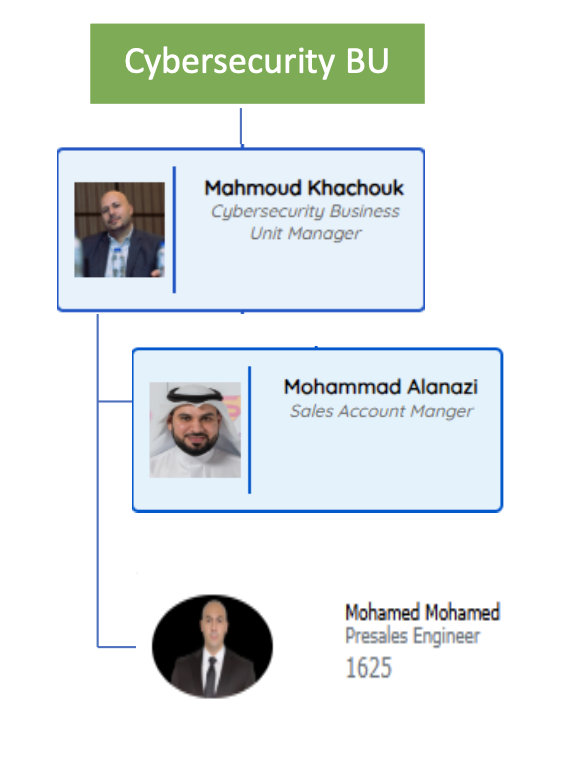
COORDINATED FRAUD & SURVEILLANCE OPERATION
| Category | Details |
|---|---|
| Fraud Methodology |
|
| Document Falsification |
|
| Surveillance Operations |
|
| Pattern of Targeting |
|
This formal legal complaint documents a sophisticated, multi-stage criminal operation orchestrated by Sejel Technology, a government-backed technology company owned by Ahmed Alawi Ghamri 🇸🇦 and led by CEO Zubair Skiredj 🇲🇦. The evidence demonstrates systematic fraud attempts, workplace surveillance, document falsification, and coordinated harassment using privileged information obtained during their hiring process.
Critical Evidence of Criminal Operations:
- Fraud call occurred minutes after Sejel HR follow-up call with exact salary knowledge
- Systematic device access and surveillance during government visits coordinated by Abu Nill 🇯🇴
- Deliberate bank account setup delays using employee named "Alaa" (Arabic for "No")
- Document falsification using Yahya Banhawi letter with forged Chamber of Commerce dates
- Coordinated MacBook theft attempt during orchestrated lunch with Yahia Ban Hawi 🇪🇬
- Package delivery deception attempting to implicate victim in suspicious activities
- High employee turnover rate indicating systematic targeting pattern
Sejel Technology Interview & Information Gathering
Initial interview with Sejel Technology. Offered 25K SAR salary. HR Rahaf Alsharif 🇸🇦 schedules follow-up meeting. Critical information shared: QID cancellation status, bank details, current salary (15K QAR), and personal circumstances. This information was later used in coordinated fraud attempt.

Coordinated Fraud Attack
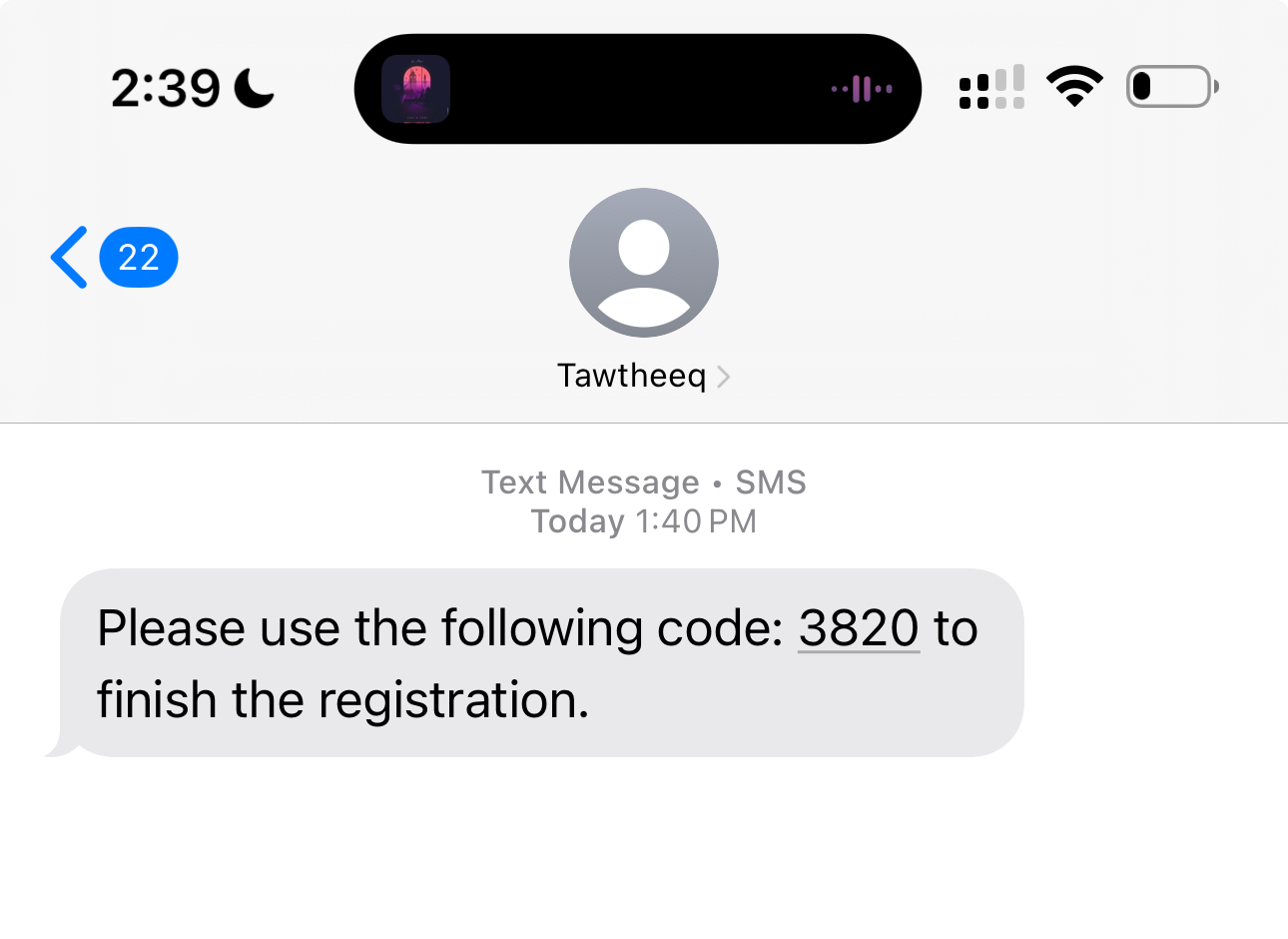
Minutes after Sejel HR follow-up call: Sophisticated fraud call from "Mohammed Ahmed" (combining Mr. Mohammed Suleiman CEO + Mr. Ahmed Ameen Head of Engineering names from previous employer). Caller knew exact details only shared with Sejel: QID cancellation, 24903 target amount, bank balance. Ahmed Ayoub 🇱🇧 coordinated the OTP crime while Rahaf Alsharif's 🇸🇦 prior call weakened defense mechanisms. WhatsApp logs confirm the precise timing correlation between HR communication and fraud attempt.
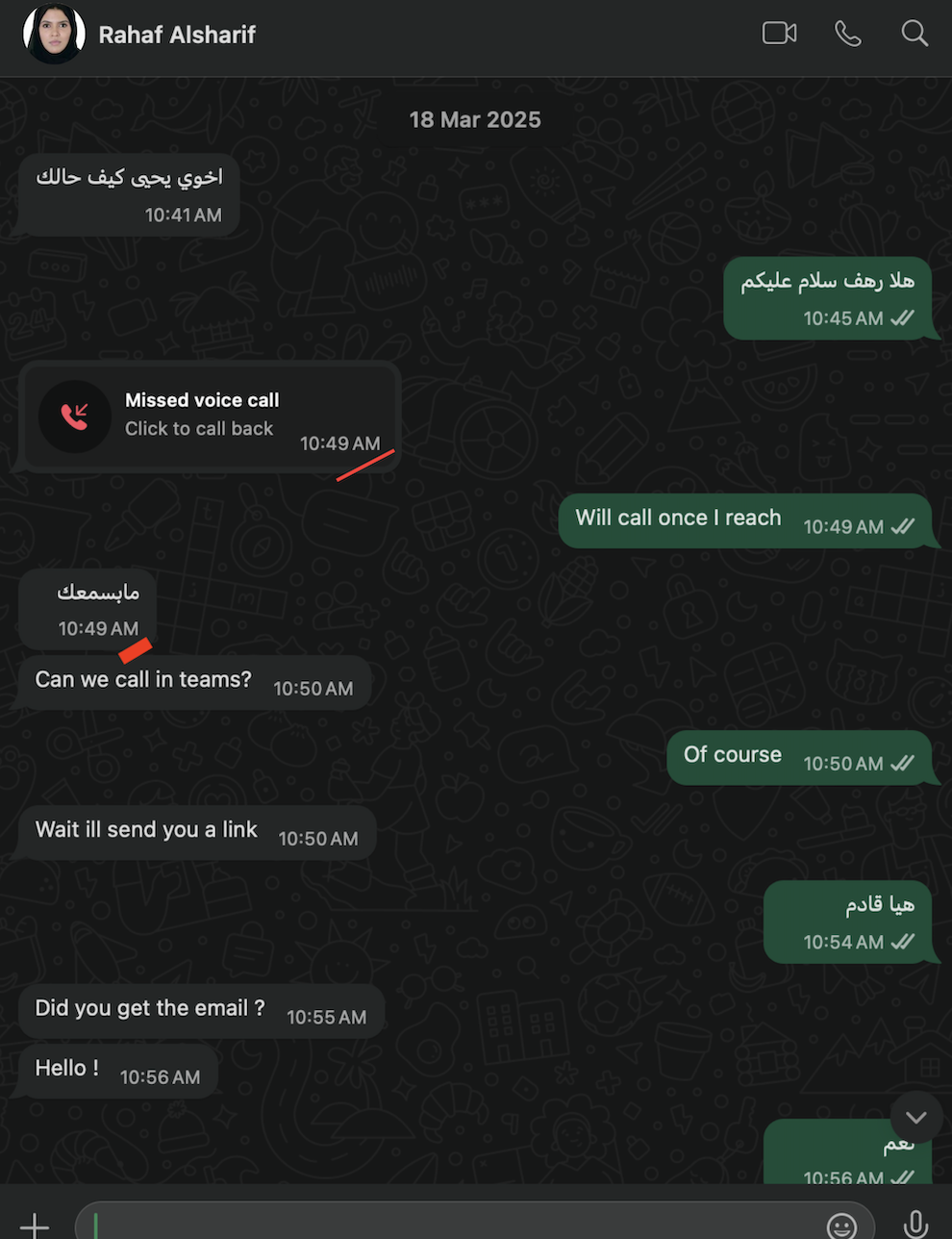
Second Round Interview with Jacob Malakh
After successfully surviving and escaping the fraud attempt, proceeded with second round interview with Jacob Malakh (Head of Delivery). The session worked exceptionally well, featuring an hour of non-stop projection of ideas and technical discussions. The fraud survival demonstrated resilience and security awareness, leading to productive engagement in the interview process.

Pre-Employment Sabotage
Attempted theft of entire backpack at Tunis airport containing MacBook Air M4, phones, passport, and documents. Timing: Day of travel to join Sejel Technology. Suspect hired "Ahmed Samara" 🇵🇸 in eastern location before victim's arrival, suggesting pre-planned coordination.
Audio Evidence:
First Day at Work - Surveillance Begins
Successfully arrival and beginning of work, placed under direct surveillance by the CBO and CBU heads, alongside Samara. Coerced into using personal macOS device, during which a system alert — a red indicator confirming active monitoring. Evidence suggests that during the visa process, an unknown party infiltrated the Hamilton Hotel in Tunisia and compromised the macOS system.

Systematic Workplace Surveillance & Data Theft
During employment at Sejel: Mahmoud Abu Nill 🇯🇴 coordinated phones data theft during government visits where devices were confiscated. Yahia Ban Hawi 🇪🇬 orchestrated lunch meeting leaving MacBook unattended for unauthorized access. Ala Elsayed (name deliberately altered to "Alaa" meaning "No") prevented bank account opening to maintain financial control. Hidden cameras deployed for continuous monitoring.

Package Delivery Deception Scheme
On the day of receiving AWS Community Builder package, an additional shipment addressed to "Mohammed" was delivered with claims it contained gold. Delivery person insisted it was for the victim alongside legitimate AWS package. This appeared to be an attempt to trick the victim into accepting suspicious packages that could later be used for false accusations or legal complications.

Fraudulent Termination & Coordinated "Accident"
Sudden termination after 1.5 months of excellent performance (delivered five government projects) using fabricated Yahya Banhawi letter scheme with falsified Chamber of Commerce dates. Immediately followed by suspicious car crash at Hilton Hotel (same location used in initial accommodation discussions). Travel companion "Mohamed" disappears completely on August 5. High employee turnover rate indicates systematic targeting pattern across multiple victims.

Hotel Saada - Orchestrated Forced Departure
Financial Entrapment & Document Retention Strategy: Access to the Suleimanyah apartment was deliberately denied due to manufactured inability to pay, forcing the victim to relocate to Hotel Essaada for the final day. This strategic move created a situation where core documents remained trapped in the Suleimanyah location, providing leverage for future manipulation.
Coordinated Exit Planning: The following day, Faisal 🇸🇦 conducted a phone call with Abu Nnill 🇯🇴 in the victim's presence, openly discussing "conclusion stamp" procedures—a calculated psychological operation to create false security. Faisal 🇸🇦 then instructed the victim to wait at the hotel, promising to deliver money. However, upon arrival, instead of financial assistance, a Qatari Airways ticket was forwarded via WhatsApp, and the victim was immediately driven to the airport for forced departure—a classic expulsion tactic designed to remove the victim from the jurisdiction while maintaining control over their documents and limiting their ability to pursue legal action.
Hotel Saada Forced Departure Evidence:

Timing Correlations
Criminal Surveillance Operations
Legal Conclusion
The systematic nature of these incidents, precise timing, document falsification, financial manipulation, and access to privileged information strongly suggests Sejel Technology, under the ownership of Ahmed Alawi Ghamri 🇸🇦 and leadership of CEO Zubair Skiredj 🇲🇦, operates as a front for sophisticated fraud and surveillance operations. The high employee turnover rate, strategic hiring patterns, coordinated termination schemes using fabricated documentation, and involvement of multiple personnel (Rahaf Alsharif 🇸🇦, Ahmed Ayoub 🇱🇧, Ala Elsayed, Abu Nill 🇯🇴, Yahia Ban Hawi 🇪🇬) indicate this is a repeating pattern targeting multiple victims. As a government-backed company, these criminal operations constitute severe violations that warrant immediate investigation, license revocation, and criminal prosecution.
Criminal Attack Vector:
- Knew QID cancellation status (shared only with Sejel)
- Had access to bank account details
- Used legitimate OTP from "Tawtheeq"
- Requested exact 24903 QAR transfer (matching Sejel offer with Germany phone code)
- Coordinated by Ahmed Ayoub 🇱🇧 minutes after Rahaf Alsharif 🇸🇦 call
Outcome: Attack prevented through security awareness. No financial loss occurred. Immediately reported to Doha Bank.
Sejel Technology Criminal Operations
- Device access and data theft during government visits (Abu Nill 🇯🇴)
- MacBook left unattended during orchestrated lunch (Yahia Ban Hawi 🇪🇬)
- Bank account setup deliberately delayed (Ala Elsayed)
- Hidden camera surveillance and following operations
- Package delivery deception scheme
- Fraudulent termination using falsified documents
- Coordinated "accident" post-termination
| Profile | Name & Position | Contact | Criminal Role |
|---|---|---|---|
 | Business Unit Manager | Coordinated in the OTP crime | |
 | HR | ralsharif@sejeltech.com +966 59 888 2821 | Called before the crime call to weaken defense |
 | HR | falghamdi@sejeltech.com +966 54 901 6177 | Ex Saudi German Health Company — core “bridge” between the victim and the mob boss. |
 | Financial Control | aelsayed@sejeltech.com +966 54 145 5014 | A rejection resource for his name |
 | Sales Manager | Coordinated the phones data theft in kharaj gov | |
 | Oracle Manager | yElbanhawy@sejeltech.com +966 56 195 7590 | Core distractor in the Mac theft attempt — handled the Egyptian food payment and controlled the lunch duration. He asked victim about Qatar, and he was told that the victim is self-made and mentioned his dad. He then talked about Oracle and CRM. |
 | Sales Specialist | +966 53 699 5517 | Involved in the Mac theft attempt, he was the one who initiated the unexpected lunch and surprisingly called the victim to join. |
Note: 14:39 GMT+3 is now GMT+1 for the victim
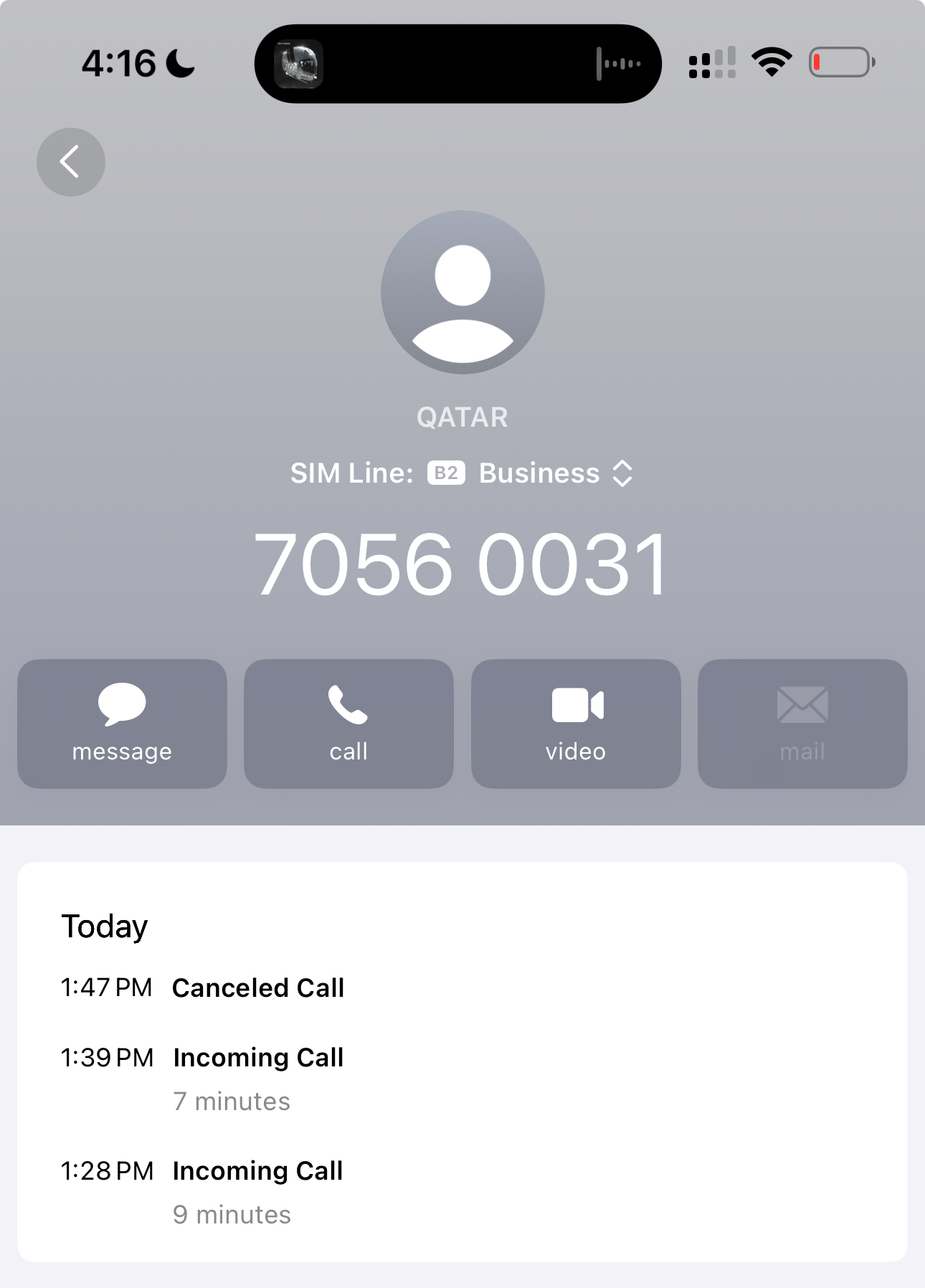
Crime number breakdown:
Documentation Status: All evidence has been preserved including screenshots, call logs, message histories, employment contracts, and falsified documents. Additional documentation available for legal proceedings.

URGENT LEGAL ACTION REQUIRED
This formal complaint documents systematic criminal operations by Sejel Technology, a government-backed company owned by Ahmed Alawi Ghamri 🇸🇦 and led by CEO Zubair Skiredj 🇲🇦 in union with CBO Subhi Omar M Al Nashwati 🇯🇴 and Ahmed Fawadh Ayoub 🇱🇧 direct report
Criminal violations include identity fraud, document falsification, unauthorized surveillance, data theft, and financial manipulation. These operations constitute severe breaches of public trust and may result in complete license revocation, termination of government contracts, and criminal prosecution of company leadership and operational personnel.
This report contains sensitive legal information and should be handled according to appropriate judicial protocols.
Generated for official legal proceedings and regulatory investigation.


Beautifully Powered by Oracle
Enterprise-grade infrastructure and reliability
Additional Workplace Context
Note: A lot of Indian contractors and outsource workers were present in the office during this period, which may have facilitated the surveillance and coordination operations.





